DMARC Protection – Domain-based Message Authentication, Reporting & Conformance (DMARC)
Contents
Overview
This file describes how the mail list server changes the From: field of an email to address enhanced email authentication policies defined by DMARC. DMARC is a technical specification to help reduce email-based abuse and spam. DMARC standardizes how email receivers authenticate email across organizations and email services such as AOL, Gmail, Yahoo, Hotmail, etc… DMARC policies are published by organizations in the public DNS and are available so mail servers understand which domains enforce DMARC policies. Information specific to the email provider is available from:
A side-effect of this standard authentication is the mismatch email list services create between the list and sender email addresses. Many email servers mark list emails as mismatched and tag them with “p=reject” which prevents these emails from being delivered. A primary goal of DMARC was to prevent spam that originates from a senders domain to be received by the same sender’s domain (e.g. AOL to AOL email, Yahoo to Yahoo, etc..) The result is an AOL subscriber sending email to listName@lists.illinois.edu may get tagged as spam and other AOL subscribers will not receive the email posting.
To comply with this new authentication mechanism, Sympa will rewrite the From: field with something that is acceptable to domains enforcing this DMARC policy.
Sympa DMARC Configuration
(Admin) > Edit List Config > DKIM – DMARC Protection
If your mail list has Yahoo, AOL, Gmail or Hotmail subscribers, you’ll need to configure DMARC to prevent AOL-to-AOL email from being tagged as spam. The default settings are configured to address this situation. The default settings are set so the Protection modes: apply to “all” email messages and rewrites the New From name format: in the “email “via Mailing List”” format.
The following section describes the different options that are available for the list owner to change based on their lists needs.
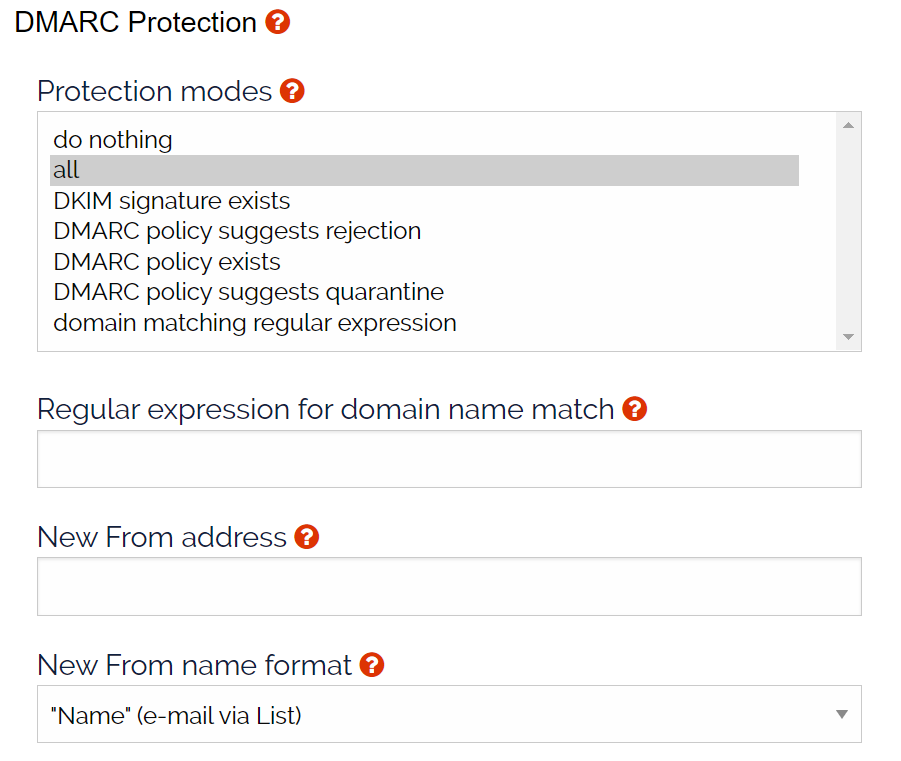
Figure 1: The default config for mail lists hosted @lists.illinois.edu.
Input fields and Values
Protection modes:
- All – apply protection to all messages
- DKIM signature exists – apply to DKIM signed email. Note: DKIM is currently off
- DMARC policy exists – apply protection when a DMARC record exists for the domain.
- DMARC policy suggests quarantine – apply protection to messages from domains where the DMARC policy is “p=quarantine”.
- DMARC policy suggests rejection– apply protection to messages from domains where the DMARC policy is “p=reject”.
- Domain matching regular expression – apply protection to any message who sender’s domain matches the regular expression (regex) in this parameter.
- Do nothing – Don’t apply DMARC protection
- The regular expression used for protection matching.
- When DMARC is triggered, the email in this field will be written to the From: field of the mail list email.
Match domain regexp:
- A regular expression used for protection matching.
- The regex for the email pattern is: “\b[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+.[a-zA-Z0-9.-]+\b”
New From address:
- When DMARC is triggered, the email in this field will be written to the From: field of the mail list email.
New from name format:
The mail list will rewrite the From: address based on list owners needs or preference.
- display name
- From: User Name <listName@lists.illinois.edu>
- display name and e-mail
- From: “User Name” (userEmail@address.com) < listName@lists.illinois.edu >
- email “via Mailing List”
- From: “User Name” (userEmail@address.com via listName Mailing List) <listName@lists.illinois.edu>
- name “via Mailing List”
- From: “User Name” <listName@lists.illinois.edu>
Example – Setting Example DMARC Reject
This example uses “DMARC policy suggests rejection” and will only be applied to domains who have the DMARC p=reject policy set on their mail servers. This configuration requires the list owner to select the policy from the Protection modes list and click the update button.
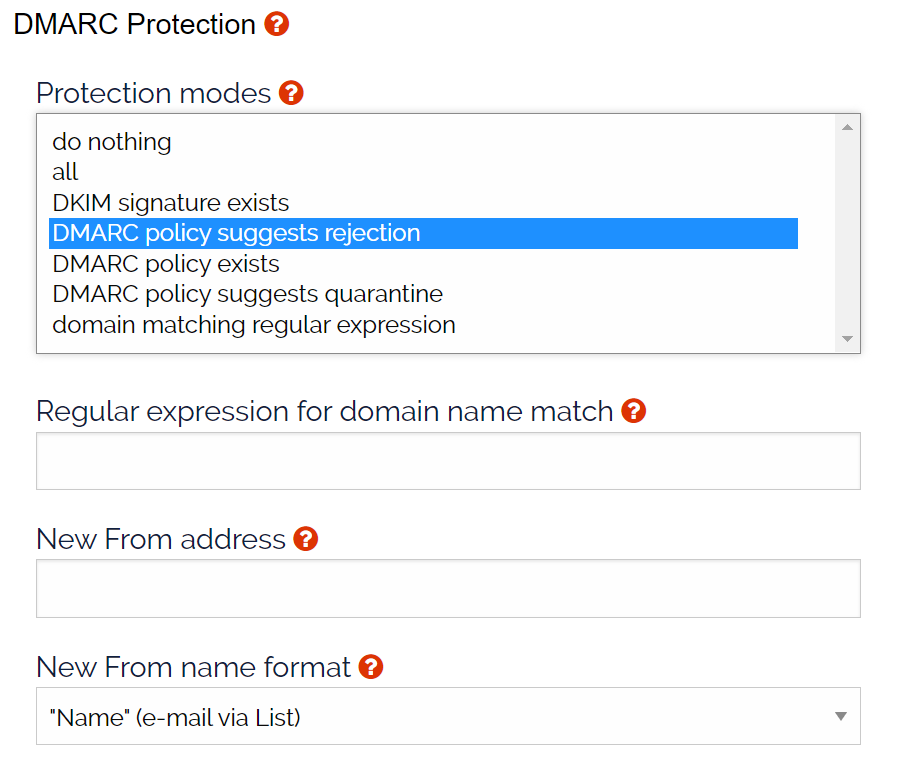
Figure 2: DMARC setting to change the From: address for mail servers set to reject.